Contpark specializes in offering a robust terminal management solution. Its platform includes features for real-time visibility, workflow automation, and security, simplifying terminal operations and increasing productivity.

Container terminals play a crucial role in international trade, facilitating the movement of goods and materials across borders. However, with the increasing globalization and the transportation of hazardous materials such as dangerous goods and chemicals, ensuring the safety and protection of these terminals has become more important than ever.
One of the key aspects of terminal security is controlling access to the premises. Access badges or identification cards are often used to restrict entry only to authorized personnel. This helps prevent any unauthorized individuals from posing a security threat or causing a disaster at the terminal.
Security guards are also an integral part of terminal security. These professionals are trained to monitor and patrol the terminal, looking out for any suspicious activities or breaches in security. They play a crucial role in maintaining order and responding promptly in case of any security incidents.
Ship-to-shore communication and coordination is another critical aspect of container terminal security. Effective communication between the terminal and the ships helps in preventing any security breaches by ensuring that the right containers are loaded and unloaded, and that the necessary security measures are in place.
Drayage and yard management are two areas that require special attention when it comes to terminal security. Drayage refers to the transportation of containers within the terminal, while yard management involves the storage and organization of containers. Both these areas need to be closely monitored to prevent any security threats or vulnerabilities.
Technological advancements have also played a vital role in enhancing terminal security. X-ray scanners and container storage monitoring systems are now commonly used to detect any potential hazards or suspicious items within containers. These technical measures help in preventing any security breaches and ensure the safe handling of goods.
Moreover, terminal administration and customs procedures have become stricter in recent years to ensure the security and integrity of the supply chain. Proper documentation, clearance, and inspection processes are in place to detect and prevent the smuggling of narcotics or other illegal goods.
Training programs for terminal personnel, including security guards, drivers, and yard workers, are also essential in preventing security incidents. These programs provide the necessary knowledge and skills to identify and respond to security threats effectively.
Overall, a comprehensive approach to terminal security, incorporating the use of technology, strict customs procedures, training programs, and effective yard management, is necessary to ensure the safety and protection of container terminals and the goods they handle. By implementing these measures, terminal operators can minimize vulnerabilities and maintain the integrity of the global trade system.
Container terminal security is of utmost importance in safeguarding the operations, personnel, and assets involved in the import and export of goods. With numerous vessels, intermodal connections, and the constant loading and unloading of containers, it is crucial to have robust security systems in place to mitigate risks and prevent any unauthorized access or breach.
One essential aspect of container terminal security is the implementation of a comprehensive surveillance system. By strategically placing security cameras throughout the terminal, monitoring can be carried out to keep a close eye on the surroundings and detect any potential intrusions or suspicious activities. The integration of intrusion detection technology and alarm systems further enhances security, ensuring prompt response to any security threats.
Automation also plays a vital role in container terminal security. Through the use of advanced technologies, such as yard management systems and automated stacking cranes, the movement of containers within the terminal can be efficiently managed, minimizing the risk of theft or tampering. The implementation of biometric security measures at security gates adds an extra layer of protection by ensuring only authorized personnel have access to restricted areas.
Additionally, conducting regular risk and vulnerability assessments is essential in identifying any weaknesses in the terminal’s security infrastructure. This includes assessing the cybersecurity measures in place to protect against potential hacking or data breaches. By continuously evaluating and improving upon these security measures, container terminal operators can stay one step ahead of potential threats.
In conclusion, container terminal security is a multi-faceted issue that requires a holistic approach to ensure the safety and protection of personnel, assets, and operations. By implementing a robust surveillance system, employing automation technologies, conducting regular risk assessments, and improving cybersecurity measures, container terminals can effectively mitigate risks and prevent potential security breaches, thus safeguarding the flow of goods and maintaining the integrity of global logistics and shipping networks.
Container terminal security is of utmost importance in ensuring the safety, protection, and smooth operations of a container terminal. With the global trade industry relying heavily on container shipments, it is crucial to implement tight security regulations and protocols to safeguard against potential threats and risks.
Container terminal security encompasses various aspects, including the security of the containers, the yard, the dock, and all areas of the terminal. Security measures such as regular inspections and customs clearance processes are implemented to ensure that all containers entering or leaving the terminal comply with safety and regulatory standards.
Unauthorized access to the container terminal is a major concern, as it can lead to theft, smuggling, or other suspicious activities. Therefore, proper security clearance procedures, biometric security systems, and intrusion detection technologies are essential to prevent unauthorized individuals from entering restricted areas.
Container inspection procedures play a crucial role in ensuring the integrity of the goods being transported. Stevedores and security guards are trained to identify any signs of tampering or suspicious behavior during the unloading, stacking, and storage of containers.
In the event of an emergency, such as a disaster or accident, container terminal security also involves effective emergency response plans and training programs to ensure the safety of personnel and minimize the impact on operations. Additionally, incident reporting and incident response protocols are implemented to address any security breaches, dangerous goods incidents, or other safety concerns.
Automation technologies are increasingly being utilized in container terminals to improve security and efficiency. Automated systems can monitor and track containers, verify their contents, and ensure proper stacking and handling procedures are followed. This not only enhances security but also minimizes the risk of accidents or damage to containers.
In conclusion, container terminal security is a multifaceted endeavor that encompasses various measures and protocols to ensure the protection and safety of container shipments. Implementing robust security measures, adhering to strict regulations, and investing in training and technology are essential for maintaining the integrity and confidentiality of the goods passing through the terminal.

In order to ensure the safety and protection of a container terminal, it is crucial to understand the various risks and threats that can arise in such an environment. Traffic management plays a vital role in maintaining order and preventing hazards from occurring. This involves implementing efficient procedures and control measures to regulate the movement of containers, trucks, and other vehicles within the terminal.
Container terminals are vulnerable to various threats, including smuggling, theft, and security breaches. Authorization control is important to prevent unauthorized individuals from accessing restricted areas and engaging in illegal activities. Access badges and security audits can help in maintaining strict control over who enters and exits the terminal.
The layout of a container terminal also plays a crucial role in its security. A well-designed terminal layout can help in mitigating risks by ensuring the effective management of cargo and the monitoring of security procedures. The use of technologies like asset tracking and container inspection systems can further enhance security measures by enabling real-time monitoring and detection of any potential threat.
Container terminals often deal with hazardous materials, such as chemicals, which pose an additional risk. Emergency drills and training programs should be conducted regularly to ensure that terminal staff and stevedores are well-prepared to handle any emergencies involving hazardous materials. This helps in maintaining the integrity of the terminal and preventing any potential accidents.
Efficiency in operations is also an important aspect of container terminal security. By implementing efficient logistics and trucking procedures, the risk of delays and security vulnerabilities can be minimized. This includes streamlining processes such as container loading and unloading, as well as establishing effective communication channels between terminals and trucking companies.
Overall, container terminal security requires a comprehensive approach that addresses the various risks and threats involved. By implementing appropriate security policies, conducting regular risk assessments, and staying vigilant, terminal operators can ensure the safety and protection of their assets, cargo, and personnel.
In order to ensure safety and protection at a container terminal, it is crucial to implement effective access control measures. These measures involve the use of various technologies and protocols to control and monitor who has access to the terminal and its facilities.
One important aspect of access control is container storage, which involves proper management of containers within the terminal. Asset tracking systems can be implemented to monitor the location and movement of containers, ensuring that they are properly accounted for and reducing the risk of theft or unauthorized access.
Another key component of access control is the use of security cameras and a surveillance system. These cameras can be strategically placed throughout the terminal, including areas such as the quay, security gate, and storage yards, to provide comprehensive coverage. The surveillance system allows for real-time monitoring and recording of activities, helping to deter criminal behavior and providing valuable evidence in case of incidents.
Access control also includes the implementation of protocols for identification and verification of individuals entering the terminal. This can involve the use of access cards, biometric systems, or other identification methods. Proper terminal layout design, with clearly marked entrance and exit points, can help ensure that only authorized personnel are granted access.
Regular emergency exercises and drills should also be conducted to test the effectiveness of access control measures and to train personnel on emergency procedures. This includes coordinating with customs and other authorities for smooth customs clearance and effective detection of contraband or potential security threats.
In addition to access control, container terminal security should also focus on incident management and response. An alarm system can be implemented to detect and notify security personnel of any breaches or incidents. Proper training should be provided to security personnel on how to respond to different situations, such as accidents during unloading or the detection of suspicious activities. Patrol routes should also be established to ensure regular inspections and surveillance of the terminal.
Container terminals play a crucial role in international trade, and ensuring their security is essential for maintaining global supply chains and preventing terrorism and other criminal activities. By implementing robust access control measures, container terminal operators can enhance the safety and protection of their facilities, assets, and personnel. Compliance with safety regulations and continuously improving security policies are essential to maintain the availability and security of container terminals.
In conclusion, container terminal security requires the implementation of strong access control measures, including the use of asset tracking, security cameras, surveillance systems, identification protocols, and emergency drills. These measures are necessary to prevent breaches, detect and respond to incidents, and ensure the safety and protection of assets, personnel, and trade operations.
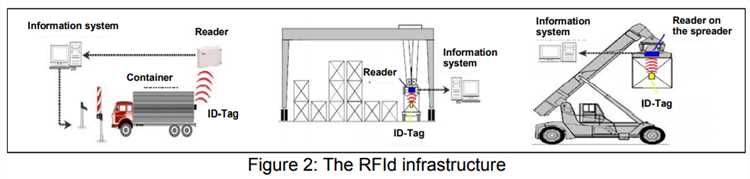
Container terminals face numerous security challenges, including theft, smuggling, and potential terrorist activity. To ensure safety and protection, terminals must implement robust surveillance and monitoring systems.
One key aspect is the monitoring of the truck queue, where chassis and containers are inspected before being allowed into the terminal. Suspicious activities or vehicles can be identified, and security clearance can be granted accordingly. High-security standards must be followed during container inspection to avoid any potential breaches.
Utilizing advanced technology and automation can significantly enhance surveillance capabilities. Surveillance equipment, such as CCTV cameras and video analytics software, can help detect and prevent unauthorized access and monitor the movement of containerships. Integration with storage and tracking systems allows for efficient container management and quick damage assessment in case of accidents.
Incident reporting plays a crucial role in maintaining terminal security. Proper documentation of any suspicious or illegal activities, including contraband detection or smuggling attempts, helps maintain the integrity of the terminal. Regular patrols can further enhance security by monitoring the wharf and yard areas.
Terminal management must establish clear security policies and procedures to handle incidents effectively. Alarm systems and intrusion detection technologies can alert security personnel in case of breaches, while explosion and hazardous materials detectors provide an additional layer of protection. Security barriers and restricted access areas also help prevent unauthorized entry.
In the event of an incident, such as a breach or an accident, incident management protocols must be followed. Quick response and recovery procedures can minimize the impact and ensure the safety of personnel and property. Regular training and drills should be conducted to ensure the preparedness of the security team.
In order to ensure safety and protection at a container terminal, securing the perimeter is of utmost importance. One of the key measures for perimeter security is the installation of an alarm system and security cameras throughout the terminal infrastructure. These technical measures provide constant surveillance of the surroundings, allowing for quick response to any potential threats.
Another critical aspect of container terminal security is the implementation of access control procedures. Authorization control and access badges are used to regulate who can enter the terminal. These measures help prevent unauthorized personnel from entering the premises and ensure the accountability of individuals present at the terminal.
Customs procedures are an integral part of container terminal security. All documentation related to the loading and unloading of containers is carefully reviewed to detect any signs of contraband or illegal activities. Communication between customs officials and terminal staff is essential to ensure that all security regulations are followed.
In addition to physical security measures, container terminal security also encompasses the prevention and detection of hazards. Fire prevention systems, such as fire alarms and conveyors, are implemented throughout the terminal to minimize the risk of fire incidents. Contraband detection technology, including X-ray scanners and metal detectors, is used to inspect containers for banned items, such as weapons or other dangerous goods.
Emergency response procedures are put in place to ensure a swift and effective reaction to any security threats or incidents at the terminal. Stevedores and other terminal personnel are trained and equipped to handle emergency situations, such as accidents or terrorist attacks. Damage assessment and management strategies are employed to minimize the impact of any security breaches.
In conclusion, container terminal security requires a comprehensive approach that combines technical measures, strict security regulations, and effective communication. By securing the perimeter, implementing access control procedures, and employing various security software and surveillance techniques, container terminals can ensure the safety and protection of their operations and personnel.
Cybersecurity has become a major concern in the container terminal industry, as terminals are vulnerable to cyber threats that can have significant consequences on operations and safety. To address this, container terminals have implemented various measures to enhance cybersecurity.
Training programs: Terminal personnel receive specialized training programs to improve their knowledge and skills in identifying and responding to cyber threats. These programs educate employees on the latest cyber attack techniques and provide them with the necessary tools to prevent and mitigate potential breaches.
Inspection and security audits: Regular inspections and security audits are conducted to identify any vulnerabilities in the terminal’s cybersecurity system. These audits help identify weak points in the network infrastructure and provide recommendations for improvement.
Access control: Container terminals have implemented strict access control measures to ensure that only authorized personnel can enter sensitive areas. This includes the use of access cards, biometric scanners, and surveillance cameras to monitor and control terminal access.
Technology: Advanced technologies such as x-ray scanning and security barriers are utilized to detect and prevent the entry of suspicious or hazardous materials into the terminal. These technologies help in the identification of potential threats and improve overall security.
Security policies and protocols: Container terminals have established comprehensive security policies and protocols to guide employees in maintaining a secure environment. These policies define the roles and responsibilities of staff and outline procedures for handling security incidents.
Security guards and patrols: Trained security guards are deployed throughout the terminal to patrol routes and monitor activities. They are trained to identify and respond to any potential security threats promptly.
Access logs: Container terminals maintain access logs that record the entry and exit of personnel, vehicles, and containers. These logs help in tracking potential security breaches and investigating any unauthorized activities.
In conclusion, container terminals recognize the importance of enhancing cybersecurity measures to ensure the safety and protection of their operations. By implementing training programs, conducting regular inspections and security audits, utilizing advanced technology, enforcing strict access control measures, establishing security policies and protocols, and deploying trained security guards, container terminals can effectively prevent and respond to cyber threats.

In order to ensure the safety and protection at a container terminal, it is essential to provide proper training and awareness programs for the personnel working at the terminal. This includes training them on how to handle different types of containers, including those carrying hazardous materials or weapons, and ensuring they are familiar with the terminal’s security procedures.
One important aspect of training is to educate personnel on the proper use of CCTV monitoring systems. They should be aware of how to effectively monitor and respond to any suspicious activities or incidents that may occur within the terminal.
Another crucial aspect of training is container inspection. Personnel should be trained on how to identify any signs of tampering or illegal activities, such as the presence of narcotics or unauthorized items within the containers.
In addition to training, regular emergency exercises should be conducted to ensure that personnel are prepared to respond swiftly and effectively in case of any security or emergency situation. This may include drills on emergency response, contingency planning, and damage assessment.
Access control is also a key element in container terminal security. Personnel should be trained on how to implement and enforce access control measures to prevent unauthorized individuals from gaining entry to restricted areas of the terminal.
Furthermore, training should also focus on the proper handling and storage of containers. Personnel should be aware of the appropriate procedures for loading and unloading containers from ships, trucks, and trailers, as well as the proper storage and handling of reefer containers.
Overall, training and raising awareness among personnel is crucial for ensuring the security of a container terminal. By equipping them with the necessary knowledge and skills, they can effectively contribute to the overall security and protection of the terminal infrastructure and operations.
Ensuring the safety and protection of a container terminal involves various security measures and collaboration with law enforcement agencies. Inspection standards are implemented to enhance security and detect any potential threats. Terminal layouts are designed to optimize security operations and ensure efficient monitoring of all activities within the terminal.
Container terminal security also relies on the training programs provided to the personnel. They are educated on security regulations, incident reporting, and response procedures. CCTV cameras are strategically positioned throughout the terminal to provide comprehensive surveillance. Perimeter security measures, such as security barriers and access control systems, help prevent unauthorized access.
Law enforcement agencies play a crucial role in container terminal security. They work closely with terminal operators to develop and implement security protocols. They conduct regular inspections, including x-ray scanning, to identify any suspicious or illegal items. Customs procedures are also integrated into the terminal operations to ensure compliance and prevent smuggling of narcotics or other prohibited substances.
In the event of a security incident or a disaster, the collaboration with law enforcement agencies becomes even more critical. They provide support in terms of recovery operations, investigation, and enforcing security regulations. Biometric security systems and advanced alarm systems are utilized to enhance container terminal security and mitigate the risk of terrorism or unauthorized access.
Container terminals also collaborate with law enforcement agencies to ensure business continuity. They develop contingency plans and regularly conduct drills to test their readiness in handling various security scenarios. These collaborations help maintain the safety and protection of the terminal, vessels, and personnel, thereby ensuring smooth shipping operations and compliance with security regulations.
Container terminal security is a crucial aspect of ensuring the safety and protection of assets and trade operations. In the event of security incidents, it is important for container terminals to have effective response procedures in place.
One key aspect of incident reporting and response is the use of advanced technologies such as x-ray scanners. These scanners can help identify any potential threats or contraband within containers, aiding in the prevention of smuggling and unauthorized access to the terminal. Additionally, the use of security cameras and authorization control systems can provide real-time surveillance and monitoring of activities within the terminal.
Container terminals must also implement strict safety regulations and standards to mitigate potential threats and vulnerabilities. Security barriers and access logs should be in place to control who enters and exits the terminal, and training programs for security guards and terminal staff should be regularly conducted to ensure they are aware of the latest security procedures and protocols.
Efficient container inspection processes play a crucial role in maintaining terminal security. Inspections should be conducted for both loaded and empty containers, and stevedores and drayage truck drivers should be required to provide appropriate documentation and undergo thorough inspections before entering or exiting the terminal.
In the event of an intrusion or security hazard, swift and effective response procedures should be followed. Terminal management should have clear guidelines and communication channels in place to coordinate the response to incidents and notify relevant authorities. Asset tracking systems can also help trace the movement of containers within the terminal and assist in identifying any potential threats or vulnerabilities.
To ensure the overall security and protection of a container terminal, a combination of advanced technologies, strict regulations, and well-trained personnel is necessary. Proactive measures in threat mitigation, thorough surveillance, and efficient response procedures will help safeguard assets and facilitate smooth trade operations within the terminal.
Regular security audits and assessments are crucial to maintaining safety and protection at a container terminal. These audits help identify vulnerabilities and areas of improvement in the terminal’s security measures.
Access logs are essential in tracking and monitoring the movement of personnel and vehicles within the terminal. They provide a record of who has accessed certain areas and can help detect any unauthorized or suspicious activities. Regularly reviewing access logs allows for quick identification and response to potential security threats.
The truck queue is another area that requires attention in terms of security. Implementing efficient traffic management systems and procedures can help prevent congestion and reduce the risk of unauthorized access to the terminal. This, in turn, enhances the overall security of the terminal.
Man-made security barriers such as fences, gates, and security checkpoints play a vital role in preventing unauthorized access to the terminal. They help maintain the integrity of the terminal layout and ensure that only authorized personnel and vehicles can enter specific areas within the terminal.
Regular training programs for terminal staff, including stevedores and crane operators, are essential for maintaining a high level of security. These programs should focus on safety regulations, incident management, emergency exercises, and cybersecurity awareness. Continuous training helps ensure that staff members are equipped with the necessary skills and knowledge to respond effectively to security threats.
Asset tracking systems are crucial for container terminals as they provide real-time information on the location and status of containers. This enhances the efficiency of terminal operations and helps identify any potential risks or security breaches.
Container terminal security is of utmost importance due to the inherent risks associated with handling a large volume of containers. The protection of these containers is essential to prevent theft, damage, and potential terrorism threats.
Security clearances play a vital role in ensuring that only authorized individuals are granted access to specific areas of the terminal. Gate passes, ID checks, and verification processes are implemented to prevent unauthorized individuals from entering restricted areas.
Terminal layouts should be designed to minimize the risk of incidents by separating pedestrian and vehicle traffic, ensuring efficient access control, and incorporating proper detection and surveillance systems.
Incident management and response protocols should be established to handle any security incidents effectively. These protocols should include procedures for evacuation, natural disasters, and suspected terrorist activities.
The ship-to-shore crane is a critical point in the container terminal where security measures should be enhanced. Increased surveillance, strict access control, and regular inspections of the crane area are necessary to prevent illegal activities or potential threats.
Cybersecurity is also an essential aspect of container terminal security, as the industry has increasingly become a target for cyberattacks. Implementing robust cybersecurity measures, such as firewalls, encryption protocols, and regularly updating software, helps protect terminal operations and prevent malicious cyber activities.
The role of a security guard at a container terminal is crucial in ensuring the safety and security of the operations. They are responsible for monitoring the terminal access, checking import and export documentation, and inspecting containers that are being loaded or unloaded from ships at the berth. With their training programs and expertise, security guards aid in safeguarding the terminal from any potential threat, whether it may be illegal intrusions, fraudulent activities, or hazardous materials.
To enhance container terminal security, advanced technology such as CCTV monitoring and security cameras are employed. CCTV monitoring allows for continuous surveillance and tracking of activities within the terminal, ensuring that any suspicious or unauthorized actions are identified and addressed promptly. Moreover, container tracking systems provide real-time visibility and traceability of containers, reducing the vulnerability to theft or unauthorized access.
Proper administration and adherence to security regulations are essential for maintaining the security of a container terminal. Regular security audits and inspections help identify any potential vulnerabilities and address them proactively. Security barriers and access control measures ensure that only authorized personnel and vehicles can enter restricted areas, minimizing the risk of intrusion. Additionally, effective communication and coordination between terminal management, customs authorities, and relevant stakeholders play a vital role in enhancing security protocols and managing any potential threats.
In the realm of container terminal security, risk management is essential for mitigating potential hazards and responding swiftly to emergencies. Emergency response procedures must be in place to handle incidents such as fires, accidents, or any other security breaches. Intrusion detection systems and alarm protocols are utilized to alert security personnel in case of any unauthorized access or suspicious activity. Adequate training and preparedness of the security staff help ensure a quick and efficient response to any potential threat.
Container terminal security is a critical aspect of ensuring the safety and protection of container terminals. With the growing trade and movement of goods, it is essential to have stringent security measures in place to safeguard against threats and illegal activities.
One of the main concerns in container terminal security is the prevention of unauthorized access. Access control measures, such as biometric security systems, can help regulate entry and ensure that only authorized personnel are allowed in restricted areas. This helps to minimize the risk of smuggling and unauthorized handling of containers.
Container security regulations play a crucial role in the protection of container terminals. Compliance with international security standards, such as the International Ship and Port Facility Security (ISPS) Code, ensures that terminal operators implement appropriate security measures to mitigate threats and risks.
Monitoring and surveillance systems, including CCTV cameras and scanners, are essential for maintaining security at container terminals. CCTV monitoring helps in keeping a watchful eye on the operations and identifying any suspicious activities that may pose a threat to the terminals. Scanners can detect dangerous goods and hazardous materials, preventing any potential risks.
Yard management and equipment security are also vital in container terminal security. Proper handling and storage of containers, as well as securing equipment like straddle carriers and tugboats, contribute to maintaining a secure environment. Implementing strict protocols for equipment usage and regular security patrols help to ensure business continuity and minimize the risk of theft or damage.
Contingency planning is another important aspect of container terminal security. Having comprehensive plans in place for potential emergencies or disruptions helps to mitigate the impact on trade and ensures the availability of necessary resources. This includes having backup systems, alternative routes, and procedures for handling hazardous materials and dangerous goods.
In conclusion, container terminal security is crucial for maintaining the safety and protection of container terminals. Ensuring compliance with security regulations, implementing access control measures, monitoring and surveillance systems, and effective contingency planning are all essential elements in preventing threats and risks. By prioritizing security, container terminals can ensure smooth operations and safeguard the trade and movement of goods.
Container terminal security refers to the measures and procedures implemented to protect container terminals from threats such as terrorism, smuggling, unauthorized access, and theft.
Some common security measures used in container terminals include the use of video surveillance cameras, access control systems, perimeter fencing, security personnel, container tracking systems, and x-ray screening equipment.
Container terminal security is important because it helps prevent and mitigate risks such as the introduction of contraband goods, terrorist attacks, and theft. It also helps ensure the safety of port personnel, the security of trade, and the smooth flow of goods through the supply chain.
A container tracking system is a technology that allows the real-time tracking and monitoring of containers as they move through the terminal and along the supply chain. It provides visibility and control over container movements, helping to prevent theft, unauthorized access, and other security risks.
Container terminal security can be improved through the implementation of advanced security technologies, regular security audits and risk assessments, training and awareness programs for terminal personnel, collaboration with law enforcement agencies, and information sharing and intelligence gathering among port operators and stakeholders.