Contpark specializes in offering a robust terminal management solution. Its platform includes features for real-time visibility, workflow automation, and security, simplifying terminal operations and increasing productivity.
In today’s interconnected world, secure Platform as a Service (PaaS) solutions have become essential for businesses and organizations seeking to protect their valuable data and ensure cybersecurity. PaaS offers numerous benefits, including interoperability, efficiency, and application usability, allowing businesses to focus on their core competencies while leaving the data protection to experts.
One of the key advantages of PaaS is its ability to provide replication and automation, simplifying the process of securing data and ensuring system reliability. With a secure PaaS, businesses can establish private VPN connections, encrypt their databases, and create disaster recovery plans to protect against unforeseen incidents.
PaaS also offers a flexible development and deployment platform, allowing businesses to control and manage their applications easily. The use of containerization and cloud-native technologies ensures rapid application testing and deployment, as well as efficient resource optimization.
With PaaS, businesses can benefit from the advanced security features offered by major providers such as Google Cloud. These features include automated encryption, network balancing, and auditing, ensuring that data remains secure at all times. Additionally, PaaS platforms provide authentication and incident response capabilities, protecting against unauthorized access and minimizing the impact of security incidents.
The use of PaaS also enables businesses to take advantage of the scalability and elasticity provided by cloud computing. PaaS platforms can handle the migration of applications and resources, allowing businesses to seamlessly upgrade their systems. The use of microservices and orchestration technology further enhances the flexibility and scalability of PaaS solutions.
In conclusion, secure Platform as a Service (PaaS) is an essential tool for businesses and organizations looking to ensure data protection and cybersecurity. Its interoperability, efficiency, and application usability allow businesses to focus on their core competencies, while replication, automation, and encryption provide simplicity, reliability, and security. With PaaS, businesses can take advantage of rapid application testing and deployment, flexible resource optimization, and advanced security features. PaaS offers a secure and reliable platform for innovation, making it an ideal choice for businesses looking to protect their data and ensure cybersecurity in today’s digital landscape.
Data protection and cybersecurity are of paramount importance in any secure platform. With the increasing dependence on technology, organizations need to ensure that their data and systems are adequately protected from cyber threats and unauthorized access. This is especially crucial in multitenancy platforms, where multiple users share the same infrastructure and resources.
A secure platform should have robust security measures in place, including encryption, strong authentication mechanisms, and firewalls, to prevent unauthorized access and protect sensitive data. It should also regularly update and patch its systems and applications to address any vulnerabilities that could be exploited by hackers.
Backup and disaster recovery capabilities are essential to ensure that data can be restored in the event of a breach or system failure. Analyzing security logs and actively monitoring the platform’s network and infrastructure can help detect and respond to potential threats in a timely manner.
Furthermore, a secure platform should provide a comprehensive authorization framework, allowing users to have different levels of access and permissions based on their roles and responsibilities. Containers and automation can help isolate and manage different workloads securely, while usability and ease of administration should be considered to ensure that security measures do not hinder productivity.
Innovation and rapid development in secure platforms have provided an opportunity for organizations to enhance their cybersecurity posture. Cloud providers like Azure offer secure and scalable infrastructure and networking capabilities, allowing organizations to focus on their core tasks while leaving the security administration to the experts.
Adhering to industry regulations and compliance requirements is paramount in a secure platform. Ensuring proper documentation, secure coding practices, and third-party assessments can help organizations meet these requirements and demonstrate their commitment to data protection and cybersecurity.
In conclusion, data protection and cybersecurity form the foundation of a secure platform. By implementing a secure architecture, robust network infrastructure, and strong authentication mechanisms, organizations can create a safe environment for their data and provide peace of mind to their users.
In today’s rapidly evolving digital landscape, organizations are constantly searching for secure and reliable solutions to manage their data and applications. A Secure Platform as a Service (PaaS) offers a cost-effective and robust solution for organizations to meet their data protection and cybersecurity needs.
A secure platform leverages innovations in virtualization, automation, and orchestration to provide a highly scalable and reliable infrastructure for organizations. It allows for the deployment and testing of applications in a secure and controlled environment, ensuring the confidentiality and integrity of data. Additionally, a PaaS platform provides built-in security services such as VPN access and datacenter optimization to enhance the overall security posture of an organization.
One of the key features of a secure platform is its simplicity and usability. It offers a user-friendly interface and supports multiple programming languages, allowing developers to easily deploy and manage their applications. The platform also provides optimization techniques such as code caching and load balancing to improve the performance and scalability of applications.
Interoperability is another important aspect of a secure platform. It enables seamless integration with existing infrastructure and services, allowing organizations to leverage their existing investments while ensuring data protection. The platform also offers robustness and reliability, ensuring that applications and data are available and accessible at all times.
In conclusion, a Secure Platform as a Service (PaaS) offers a comprehensive and cost-effective solution for organizations to ensure data protection and cybersecurity. With its innovative technologies, built-in security services, and user-friendly interface, a secure platform provides organizations with the necessary tools to develop, deploy, and manage their applications securely and efficiently.
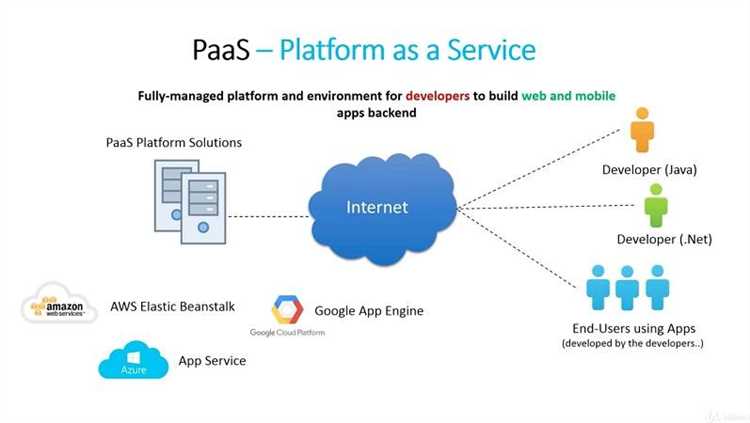
When it comes to data protection and cybersecurity, using a secure Platform as a Service (PaaS) can offer numerous benefits for organizations.
In conclusion, utilizing a secure PaaS solution provides organizations with the opportunity to enhance their data protection and cybersecurity measures. It offers reliability, usability, integration, data protection, scalability, and continuous delivery capabilities. By leveraging these benefits, organizations can ensure the security and efficiency of their applications and services while meeting regulatory requirements and reducing operational risks.
In today’s digital age, the secure storage and protection of data has become a paramount task for organizations across all industries. With the increasing reliance on cloud computing services, it is essential to have a secure platform that can effectively manage and protect sensitive information.
A cost-effective approach to secure data storage is through the use of secure platform as a service (PaaS) solutions. These platforms offer a highly scalable and robust environment for hosting applications and storing data. By leveraging the power of cloud computing, organizations can achieve cost optimization and scalability without compromising on data security.
One such secure platform is Azure, offered by Microsoft. With its comprehensive set of services, Azure provides a secure and reliable environment for hosting applications and managing databases. Its containerization technology ensures that each application runs in its own isolated environment, enhancing security and preventing unauthorized access.
Additionally, Azure offers robust encryption and authentication capabilities to ensure the confidentiality and integrity of data. Organizations can utilize Azure’s auditing and compliance features to monitor and manage data access, ensuring regulatory compliance and data governance.
Google Cloud Platform is another secure platform that offers innovative solutions for data storage and cybersecurity. Its highly scalable architecture allows organizations to scale their resources based on demand, ensuring optimal performance and cost efficiency.
Google Cloud Platform provides a range of secure storage services, including databases and object storage, with built-in encryption and access control mechanisms. Its agile runtime environment supports a variety of programming languages and allows for the rapid development and deployment of applications.
Furthermore, Google Cloud Platform offers strong authentication and access control mechanisms, ensuring only authorized personnel can access sensitive data. Its comprehensive set of APIs and developer tools enable seamless integration with existing systems and facilitate secure data exchange.
In conclusion, safe and secure data storage solutions are crucial for organizations to protect their data from cyber threats and ensure compliance with privacy regulations. Secure platform as a service (PaaS) solutions, such as Azure and Google Cloud Platform, offer robustness, cost-effective management, and scalability for data storage and application hosting. By leveraging these platforms, organizations can optimize their operations while maintaining the highest levels of data protection and cybersecurity.
In a secure Platform as a Service (PaaS) environment, encryption and authentication play vital roles in ensuring data protection and cybersecurity. Managed encryption solutions provide control over data access and prevent unauthorized users from gaining access to sensitive information. By implementing encryption techniques, organizations can securely store and transmit data, safeguarding it from potential threats.
Authentication mechanisms verify the identity of users and ensure that only authorized individuals can access the PaaS platform. With multi-factor authentication and role-based access controls, organizations can strengthen their security posture and mitigate the risk of unauthorized access. This ensures that only legitimate users, who have been authenticated through various means, can interact with the platform.
Cloud-based secure platforms offer a cost-effective solution for organizations, as they eliminate the need for investing in extensive infrastructure and server management. Scaling resources in a secure PaaS environment becomes an automated process, allowing organizations to quickly adapt to changing demands without compromising data security.
Disaster recovery and backup solutions are essential in a secure PaaS environment, ensuring that data remains protected and accessible even in the event of a catastrophe. Automated workflows and monitoring dashboards provide real-time insights into system performance and security, enabling organizations to proactively address any potential vulnerabilities or breaches.
The framework of secure PaaS platforms incorporates serverless architectures, containerization, and networking solutions. These technologies ensure consistency in service delivery, optimize performance, and enable easy configuration and monitoring of applications. Orchestration and analytics tools support rapid deployment, testing, and load balancing, enhancing the agility and scalability of the platform.
In addition to encryption and authentication, authorization mechanisms govern user access and actions within the secure PaaS environment. Role-based access control and fine-grained permissions ensure that users only have access to the resources and data they require, minimizing the risk of data breaches.
Furthermore, secure PaaS platforms offer auditing capabilities to track and monitor user activity, providing a comprehensive audit trail of data interactions and system changes. Firewall protection and secure networking protocols ensure that data remains secure even when transmitted over public networks.
Overall, encryption and authentication are essential components of a secure PaaS platform. Combined with other security measures, they provide organizations with a robust and secure environment for their data and applications.
In order to ensure data protection and cybersecurity in the context of Secure Platform as a Service (PaaS), it is essential to implement a range of security measures for application development and deployment. These measures are crucial for maintaining the usability, availability, management, and extensibility of the platform while also protecting against potential security threats.
One important security measure is the implementation of firewalls, which act as a barrier between the external world and the platform’s internal network. By monitoring and controlling incoming and outgoing network traffic, firewalls help to prevent unauthorized access and protect the platform from malicious attacks.
Analytics tools play a vital role in identifying and addressing potential security vulnerabilities. Task automation and scalable analytics platforms can assist in detecting suspicious activities and providing real-time alerts, allowing for prompt responses and mitigating the impact of any security threats.
Containerization is another essential security measure that can help ensure a secure platform. By isolating applications and their dependencies within separate containers, containerization provides a level of security and control over the application environment. It helps to limit the potential damage that can be caused by any security breaches and allows for better management and scaling of deployments.
Authentication and access control mechanisms are critical for ensuring only authorized individuals have access to the platform. Strong authentication methods, such as multifactor authentication and single sign-on, can provide an additional layer of security. Role-based access control helps to define fine-grained access privileges based on user roles, restricting unauthorized access and preventing potential security breaches.
Implementing continuous integration and continuous deployment (CI/CD) pipelines is an effective way to ensure the security and stability of application deployments. CI/CD pipelines automate the build, testing, and deployment processes, enabling rapid, controlled, and secure deployments. By integrating security checks at each stage of the pipeline, potential vulnerabilities can be identified and addressed early on.
Ensuring compliance with relevant regulatory requirements is another crucial aspect of a secure platform. The platform should have mechanisms in place to monitor and enforce compliance with data protection regulations, privacy laws, and industry standards. Compliance auditing, logging, and reporting functionalities can assist in demonstrating adherence to these requirements.
Secure platform solutions should also include robust disaster recovery and backup mechanisms. Regular data backups can help in mitigating the impact of potential data breaches or system failures. Secure storage and database solutions should be implemented to ensure the confidentiality, integrity, and availability of data.
Furthermore, secure platforms should foster interoperability by supporting seamless integration with other systems and services. This enables the exchange of data and functionalities between different platforms and applications, while also promoting secure data transfer and communication.
The ownership and management of the platform should be well-defined, with clear roles and responsibilities. This helps to ensure accountability and facilitate effective governance over the platform, enhancing overall security.
By leveraging secure platform solutions and implementing these security measures, organizations can take advantage of the opportunities offered by PaaS while ensuring data protection and cybersecurity in their application development and deployment.
Access, Ownership, and Governance: In the cloud-native environment, secure platform providers ensure that the ownership and access to data resources are strictly regulated and governed. By implementing robust data protection regulations and providing built-in security features, these platforms enable organizations to maintain control over their data while ensuring compliance with data protection regulations.
Flexible and Rapid Deployment: Secure platform as a service (PaaS) solutions offer a flexible and rapidly deployable environment for the development and deployment of applications. With the use of modern technologies such as serverless computing and container orchestration, organizations can quickly build, deploy, and scale applications with ease while maintaining a high level of security and compliance.
Secure Storage and Reliability: Secure platforms provide highly reliable storage solutions that ensure the security and integrity of data. With advanced encryption and data replication techniques, these platforms enable organizations to securely store their data while ensuring compliance with data protection regulations.
Usability and Control: Secure platforms offer user-friendly interfaces and control mechanisms that enable organizations to manage and control their data securely. With features such as access controls, auditing capabilities, and data lifecycle management, organizations can ensure that their data is protected and compliant with data protection regulations.
Innovation and Compliance: Secure platforms not only offer robust security measures but also foster innovation by providing support for various programming languages and technologies. This enables organizations to develop and deploy innovative applications while ensuring compliance with data protection regulations.
Scalability and Balancing: Secure platforms offer scalability and load balancing capabilities, allowing organizations to handle increasing data volumes and user traffic while ensuring data protection and compliance. With the ability to auto-scale resources and distribute workloads efficiently, these platforms provide a secure and high-performance environment.
Auditing and Compliance: Secure platforms provide auditing capabilities that enable organizations to monitor and track data access, ensuring compliance with data protection regulations. By generating comprehensive audit logs and reports, these platforms help organizations maintain transparency and demonstrate compliance.
Mobile and Web App Development: Secure platforms support the development of mobile and web applications, providing secure and reliable hosting environments. With features such as secure API integration, authentication mechanisms, and secure cache management, these platforms ensure the protection of sensitive user data.
Azure as a Secure Datacenter: Microsoft Azure, a leading secure platform provider, offers a highly secure and compliant datacenter environment. With advanced security features, including threat detection, network isolation, and data encryption, Azure provides organizations with a secure and reliable platform for their data storage and processing needs.

As organizations continue to embrace innovation and adopt cloud-native solutions, the need for robust security measures becomes paramount. In the context of a secure Platform as a Service (PaaS) environment, monitoring and auditing tools play a crucial role in ensuring data protection and cybersecurity.
With the ability to deploy highly secure and scalable applications, a secure PaaS platform provides a solid foundation for organizations to build their software infrastructure. It offers features like automated patching and software updates, seamless integration, and secure runtime environment, minimizing the risk of vulnerabilities and unauthorized access.
Monitoring tools in a secure PaaS platform allow for real-time visibility into the performance and security of applications and infrastructure. These tools enable comprehensive monitoring of resources, networking, and microservices deployments, providing valuable insights into any potential incident or security breach. By leveraging these monitoring capabilities, organizations can proactively identify and mitigate risks, ensuring the ongoing security of their deployments.
Audit tools are equally essential in securing a PaaS environment by offering visibility into the access and actions performed within the platform. These tools facilitate authentication, authorization, and governance, ensuring that access to sensitive resources is securely managed. The audit logs generated by these tools enable organizations to track and investigate activities, promptly identifying any unauthorized access or potential security violations.
Some leading PaaS providers, such as Azure and Google Cloud, offer a range of monitoring and auditing tools to enhance the security of their platforms. These tools include authentication and authorization frameworks, disaster recovery solutions, secure API management, and collaboration workflows. The compatibility and ease of use of these tools enable organizations to adopt agile methodologies, support serverless architectures, and create private networking environments, all while maintaining a strong security posture.
In conclusion, monitoring and auditing tools play a critical role in securing a PaaS environment. They provide organizations with real-time visibility, automated security measures, and robust authentication and authorization functionalities. By leveraging these capabilities, organizations can ensure the protection of their data and infrastructure, confidently embracing the benefits of a secure platform.
Ensuring the security of data and maintaining strong cybersecurity practices are critical in the PaaS environment. With the agility and innovations that PaaS platforms bring, it is essential to have robust security incident response and recovery processes in place.
Integrations and deployments on a secure platform must be carefully managed to protect sensitive data from potential threats. Version control and continuous patching are essential to keep the server and applications up to date and secure. Automated workflows and orchestration can help streamline security incident response and recovery tasks, ensuring a fast and effective response.
In a multitenancy environment, where multiple users share resources, ensuring data isolation and secure access control is vital. The implementation of containerization and secure identity management systems can add an extra layer of protection to prevent unauthorized access to sensitive data and critical system resources.
Disaster recovery and business continuity planning should be an integral part of the PaaS architecture. Regular data backups, load balancing, and elastic scalability help ensure data availability and minimize downtime in the event of a security incident or system failure. The use of cache and load balancing mechanisms can help optimize system performance while providing redundancy.
Continuous monitoring and analytics can help detect and mitigate security threats in real-time. A built-in dashboard with comprehensive security analytics provides administrators with visibility into potential vulnerabilities and ongoing security incidents, allowing them to take prompt action.
The governance and control of the PaaS environment are crucial to maintaining a secure platform. Strong access controls, data encryption, and secure development practices, such as secure coding and vulnerability scanning, should be integrated into the PaaS development lifecycle. Regular security audits and vulnerability assessments can help identify and address any potential weaknesses.
In a PaaS environment, upgrading and migrating applications to newer versions is an important task that requires careful planning to maintain security. Secure VPN connections and secure data migration tools can facilitate a seamless application upgrade process while ensuring data protection.
Overall, security incident response and recovery in PaaS platforms provide an opportunity for organizations to embrace the benefits of innovation and agility while maintaining robust cybersecurity practices. By implementing secure development and deployment processes, organizations can confidently leverage the advantages of PaaS while protecting their data and minimizing security risks.
When it comes to secure platform as a service (PaaS), collaborating with trusted providers is essential. Secure PaaS providers offer a range of virtualization, hosting, and access tools to ensure the resilience and recovery of your data. By leveraging their platform and governance features, you can ensure that your data remains protected throughout its lifecycle.
One key aspect of collaborating with secure PaaS providers is their commitment to compatibility and extensibility. These providers constantly update their platforms to support the latest technologies and innovations, ensuring that you can seamlessly integrate with other cloud-native services and tools. With features such as managed firewall and identity, they provide end-to-end control over your data’s security.
Another advantage of working with secure PaaS providers is their focus on automation and orchestration. These providers offer automated tools and task management capabilities, allowing you to streamline your development and deployment workflows. With their containerization technology, they enable the efficient scaling and management of microservices and applications, making your development process agile and scalable.
Moreover, collaborating with secure PaaS providers ensures compliance with industry regulations. These providers have robust network and load management capabilities, allowing you to meet regulatory requirements regarding data security and privacy. Their scalability and elasticity features ensure that your applications can handle increased workloads without compromising on performance or security.
In conclusion, collaborating with secure PaaS providers brings numerous benefits to your data protection and cybersecurity efforts. Their platform and governance features, compatibility, automation, and control tools, as well as network scalability, enable you to build and manage secure and resilient applications. By leveraging their expertise and innovations, you can confidently navigate the ever-evolving landscape of data security and stay ahead of potential threats.
PaaS platforms provide a secure and efficient environment for deploying applications and managing data. To ensure data protection and cybersecurity, following best practices is crucial.
Implement strong encryption techniques to safeguard data both at rest and in transit. Use access control mechanisms to restrict unauthorized access and grant permissions only to authorized users.
Implement regular backup procedures to ensure data integrity and recovery in the event of an incident. Regularly test backup and recovery procedures to ensure their effectiveness.
Ensure the security of network infrastructure and servers by implementing firewalls, intrusion detection systems, and regularly updating security patches. Employ secure protocols for network communication to prevent unauthorized access.
Implement secure coding practices and perform regular security testing for applications deployed on the PaaS platform. Monitor and log application activities to detect and respond to potential security threats.
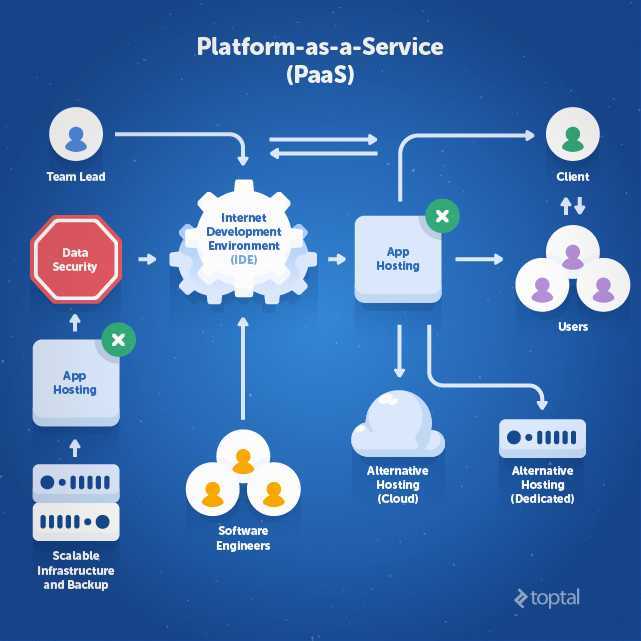
Ensure strong isolation and separation of data between tenants in a multitenant environment. Employ containerization technology to provide enhanced security and isolation for applications and their data.
Implement robust monitoring and auditing mechanisms to track system activities, detect abnormal behavior, and investigate security incidents. Regularly review audit logs to identify potential vulnerabilities.
Ensure seamless integration and interoperability with other systems and platforms by following industry standards and protocols. Regularly test and validate integrations to maintain compatibility and reliability.
Utilize the scalability and performance capabilities of the PaaS platform to efficiently handle increasing data volumes and user loads. Optimize resource allocation and adopt technologies like serverless architecture to improve efficiency.
Promote collaboration among developers and system administrators to ensure a comprehensive approach to data protection. Foster an environment that encourages the use of extensible solutions and rapid development.
By following these best practices, organizations can ensure the secure platform as a service (PaaS) with robust data protection and cybersecurity measures in place.
Platform as a Service (PaaS) is a category of cloud computing services that provide a platform for users to develop, run, and manage applications without the complexity of building and maintaining the infrastructure typically associated with developing and launching an app.
Data protection is important in PaaS to ensure the confidentiality, integrity, and availability of data stored, processed, and transmitted within the platform. It helps to prevent unauthorized access, data breaches, and loss of data.
Data encryption in PaaS can be implemented by using encryption algorithms to encrypt data before storing or transmitting it. PaaS providers may offer built-in encryption features or allow users to integrate third-party encryption tools into their applications.
Regular data backups in PaaS provide a means to recover data in case of accidental deletion, hardware failures, natural disasters, or other data loss events. It helps to ensure business continuity and minimize downtime.
Access controls and authentication mechanisms in PaaS can be implemented by using robust identity and access management systems. This includes using strong passwords, implementing multi-factor authentication, and assigning appropriate user roles and privileges.