Contpark specializes in offering a robust terminal management solution. Its platform includes features for real-time visibility, workflow automation, and security, simplifying terminal operations and increasing productivity.
With the increasing importance of internet security, it is crucial to understand the Secure Sockets Layer (SSL) and its role in safeguarding online communications. SSL is a technology that uses cryptography to protect data during transmission, providing a secure and encrypted connection between a client and a server. The SSL authentication process ensures that both parties are authenticating each other’s identity before establishing a secure communication channel.
The SSL authentication process, also known as the SSL handshake, is a series of steps that occur between the client and the server when establishing a connection. During this process, the client and the server exchange information and negotiate the encryption algorithm and the keys to be used for the encrypted communication. This ensures that only the intended recipient can decrypt and read the information, guarding against potential vulnerabilities.
One of the key components of SSL is the use of digital certificates. These certificates verify the identity of the server and establish trust between the client and the server. The SSL vulnerability management system plays a vital role in protecting against potential SSL vulnerabilities and ensuring the integrity and trustworthiness of the certificates used in the authentication process.
The SSL vulnerability assessment, conducted by an SSL vulnerability administrator, helps to identify any weaknesses or vulnerabilities in the SSL implementation. This assessment is crucial in preventing data breaches and ensuring that the communication is secure. The SSL vulnerability software and the SSL vulnerability researcher work together to analyze potential vulnerabilities and develop solutions to further enhance the security of the SSL technology.
All in all, understanding the SSL and its secure authentication process is essential in today’s world of cybersecurity. SSL not only protects the data confidentiality during communication but also provides a secure environment for users to trust and engage with online platforms. It is important to have SSL vulnerability analysis and SSL vulnerability management systems in place to defend against potential SSL vulnerabilities and ensure a safe and guarded online experience for all.
What is the Secure Sockets Layer (SSL)?
Secure Sockets Layer (SSL) is a protocol that provides secure communication between two entities, typically a client (browser) and a server. It ensures that the data transmitted between them remains encrypted and confidential. SSL creates a secure connection by using SSL certificates, which are digital documents that authenticate the identity of the website or server.
SSL Secure Authentication Process
The SSL authentication process involves several steps to secure the communication between the client and the server, providing protection against cybercrime and data breaches:
This SSL secure authentication process not only helps to safeguard the data transmitted between the client and the server but also verifies the authenticity of the server, ensuring that users are connecting to the intended and secure website. By implementing SSL, websites can provide a secure environment for users, protecting them from potential vulnerabilities and maintaining the confidentiality of their data.
Secure Sockets Layer (SSL) is a crucial component in maintaining secure online communication. It plays a vital role in protecting sensitive information such as personal details, financial data, and login credentials from falling into the wrong hands. SSL acts as a shield between the web browser and the website, establishing a secure and encrypted connection that prevents any unauthorized access or interception.
One of the key elements of SSL is the secure authentication process it employs. During this process, SSL verifies the identity of the website by checking its SSL certificate. It ensures that the website is legitimate and not a fake one created by hackers. This authentication process is carried out by an SSL vulnerability coordinator who ensures that the website is a safe and protected source of communication.
When a user initiates a connection to a website, SSL verifies the website’s identity using an encryption algorithm. The SSL vulnerability server sends a unique SSL certificate to the web browser, which the web browser uses to establish a secure connection.
Once the SSL connection is established, all communication between the user and the website is securely encrypted, making it impossible for any cybercriminal or hacker to intercept or decipher the information being transmitted. This encryption ensures privacy and confidentiality, giving users the confidence that their sensitive data is being transmitted securely.
In addition to securing online communication, SSL is also essential for secure email and file transfers. By employing the SSL authentication process, users can protect their sensitive emails and files from being accessed or tampered with by unauthorized individuals.
In conclusion, SSL and its secure authentication process are crucial components of cybersecurity. They defend against potential attacks and ensure that online communication remains safe and protected. By implementing SSL, users can have peace of mind knowing that their information is locked and secure during transmission.
How does SSL encryption work?
SSL encryption ensures a secure connection between a user and a system, protecting the privacy of their communication. When a user requests to access an SSL-secured website, their browser and the web server initiate an SSL handshake. During this process, the server sends its digital certificate to the browser, which contains a public key. The browser validates the certificate and generates a symmetric encryption key. This key is used to encrypt and decrypt data exchanged between the browser and the server, ensuring that it cannot be intercepted by cybercriminals.
SSL secure authentication process
The SSL secure authentication process involves the validation of digital certificates to ensure the authenticity and integrity of the communication. When a user accesses a website with an SSL certificate, the browser checks the validity of the certificate by verifying the issuer’s digital signature and ensuring that it has not expired or been revoked. If the certificate is valid, the browser establishes a secure connection with the server using the encryption algorithm specified in the certificate. This secure connection allows for private and secure transfer of data, guarding against cyber threats and ensuring internet security.
To support SSL vulnerability solutions, SSL vulnerability engineers work to identify and fix any potential vulnerabilities in the SSL protocol. Their work involves constant monitoring of the SSL vulnerabilities online and developing defensive measures to guard against cyber attacks. With their expertise, SSL vulnerability engineers play a crucial role in enhancing the security of SSL-secured communications.
SSL (Secure Sockets Layer) certificates play a crucial role in the secure authentication process of websites. SSL technology ensures encrypted communication between a web browser and the website server, providing a high level of data confidentiality and integrity.
An SSL certificate acts as a shield, defending against cybercriminals who may attempt to intercept or manipulate sensitive information transmitted over the internet. It serves as a defensive measure, protecting the communication channel and ensuring that only authorized parties can access the transmitted data.
During the SSL secure authentication process, the SSL handshake takes place, which is a series of protocols that establish a secure connection between the web browser and the website server. The SSL handshake verifies the authenticity of the website and encrypts the data exchanged between the two parties.
By encrypting the data, SSL technology ensures that any intercepted information remains unreadable to unauthorized individuals. This encryption acts as a safeguard, preventing potential identity theft and ensuring the secrecy of the transmitted data.
SSL certificates also provide website security in terms of data integrity. Through a combination of encryption and verification, they guarantee that the transmitted data remains unchanged and unaltered during transmission. This protects against data manipulation and helps maintain the trust of users in the website’s information.
To ensure the effectiveness of SSL certificates, organizations employ SSL vulnerability analysts and SSL vulnerability support to identify and address any potential weaknesses or vulnerabilities in the SSL implementation. This helps keep the SSL connection guarded and strengthens the overall security of the website.
In addition to SSL certificates, organizations further enhance their website security by implementing firewalls and other secure network measures. These defensive layers work in conjunction with SSL technology to provide a covered and protected environment for data transmission, reducing the risk of unauthorized access and data breaches.
SSL certificates are a crucial element in ensuring the security of online communication and data transfer. There are different types of SSL certificates, each offering a different level of security and protection.
The SSL secure authentication process involves several steps to ensure the secure transmission of data.
Understanding the types of SSL certificates and the SSL secure authentication process is essential for ensuring a robust and protective online environment. By implementing SSL technology and following proper validation processes, organizations can strengthen their defense against cybercrime and safeguard sensitive data from unauthorized access.
The SSL handshake process plays a crucial role in establishing a secure connection between a client and a server. It involves several steps that are designed to ensure the authenticity and confidentiality of the communication.
The SSL protocol works as a secure layer protecting data from unauthorized access. Its purpose is to safeguard the sensitive information exchanged over the internet, such as personal and financial data, ensuring its confidentiality and integrity.
During the SSL handshake, the client and the server exchange information to verify each other’s identity and establish a secure connection. The client sends a request to the server, and the server responds with its SSL certificate, which contains the server’s public key.
The SSL certificate is issued by a trusted authority and serves as proof of the server’s identity. It is a crucial element in the SSL secure authentication process, as it allows the client to verify the server’s legitimacy before establishing the connection.
The SSL vulnerability expert, known as the SSL vulnerability administrator, plays a significant role in managing the SSL vulnerability of a system. They ensure that the SSL certificates are up to date and monitor any potential threats or vulnerabilities. They also conduct regular SSL vulnerability testing to identify and fix any weaknesses in the SSL encryption.
Once the server’s identity is verified, the client and the server perform a series of encryption and decryption operations using symmetric encryption. This ensures that the data exchanged between them remains secure and confidential, even if intercepted by an unauthorized third party.
The SSL protocol, along with the HTTPS (Hypertext Transfer Protocol Secure) technology, provides the necessary safety measures to protect sensitive information online. It enables secure email communication, secure login to websites, and other applications that require data confidentiality.
In conclusion, the SSL handshake process and SSL secure authentication process are essential in establishing a secure connection and protecting sensitive data. By verifying the identity of the server and utilizing encryption technology, the SSL protocol safeguards the communication from threats and data breaches, ensuring the privacy and integrity of online transactions.
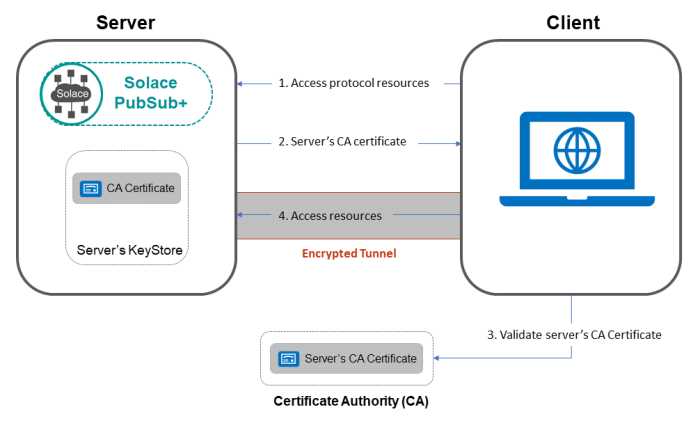
The secure authentication process of SSL certificates is essential in protecting online communication and guarding against cybercrime threats. When a user connects to a secure server through HTTPS, the server presents its SSL certificate as proof of its legitimacy and safety. To ensure the certificate is authentic and secure, it undergoes a validation process carried out by trusted certificate authorities.
Certificate authorities (CA) play a critical role in establishing the trustworthiness of SSL certificates. These authoritative firms verify the identity of the certificate requester and validate the information contained within it, ensuring that it belongs to the indicated server. The CA uses protocols such as the Public Key Infrastructure (PKI) and encryption algorithms to create a digital signature, adding an extra layer of validation.
SSL vulnerability analysts continuously assess certificate authorities and their processes to detect and mitigate any potential vulnerabilities or weaknesses. This defensive approach aims to maintain the security and resistance of the SSL certificates against threats, ensuring the safety of online transactions and communications.
Once the certificate has been validated and safeguarded by the CA, it can be used to authenticate the server during the SSL secure authentication process. The certificate acts as a trust anchor, assuring clients that they are communicating with a legitimate and secure server. This verification process establishes an encrypted connection, creating a secure environment for transmitting sensitive information such as login credentials or credit card details.
To verify a SSL certificate, users can rely on several indicators. The presence of «https://» at the beginning of the URL indicates the use of an SSL certificate to protect data transmission. Users can also click on the padlock icon in the browser’s address bar to view the certificate details, including the certificate authority and its expiration date. Additionally, SSL certificate providers such as SSLShopper offer online resources for users to verify the authenticity and validity of SSL certificates, providing further assurance in their secure authentication process.
When it comes to protecting sensitive data transmitted over the internet, SSL/TLS protocols play a crucial role. These protocols encrypt data sent between a user’s browser and a website, ensuring that it remains confidential and inaccessible to unauthorized individuals.
One of the key components of SSL/TLS protocols is the secure authentication process. This process verifies the identity of the website and prevents cybercriminals from impersonating trusted entities. It uses digital certificates to authenticate the website, establishing a secure connection between the user and the server.
To fortify the SSL vulnerability system, websites employ various security measures. One such measure includes the use of firewalls that filter incoming and outgoing network traffic, preventing unauthorized access and potential data breaches. Additionally, implementing SSL vulnerability testing and utilizing SSL vulnerability software can help identify and address any security gaps or vulnerabilities in the system.
A crucial step in ensuring a secure website is conducting regular SSL vulnerability assessments. These assessments, conducted by SSL vulnerability consultants or through SSL vulnerability checkers, evaluate the website’s security posture and identify any potential weaknesses or vulnerabilities that could be exploited by hackers or malware.
By taking the necessary steps to secure their website using SSL/TLS protocols and staying proactively guarded against SSL vulnerabilities, website owners can significantly reduce the risk of data breaches, identity theft, and other cyber attacks. This allows users to browse and interact with the website securely, knowing that their information is safe and protected.
SSL, or Secure Sockets Layer, is a crucial technology for securing connections on the internet. However, it is not without its vulnerabilities. Understanding these vulnerabilities and taking steps to mitigate them is essential for maintaining a secure network environment.
The authentication process is a crucial step in establishing a secure SSL connection. It ensures that the identity of the server is verified, and the connection is encrypted using SSL technology.
One common vulnerability in the authentication process is a man-in-the-middle attack, where an attacker intercepts the communication between the client and the server. To defend against this, it is important to use SSL certificates that are issued by trusted Certificate Authorities and implement a robust Public Key Infrastructure.
An SSL vulnerability tool, such as an SSL vulnerability scanner or SSL vulnerability management system, can help identify any potential vulnerabilities in the SSL connection. Regularly scanning and monitoring for vulnerabilities will assist in protecting the network from potential threats.
In addition to using SSL encryption, it is essential to protect the server from other vulnerabilities, such as malware or unauthorized access. Implementing a firewall and regularly updating the server’s software and security patches are essential steps in defending against these types of vulnerabilities.
In conclusion, understanding the common vulnerabilities in SSL and taking appropriate measures to mitigate them is crucial for ensuring the privacy and data protection of a secure network. Implementing SSL technology with a strong authentication process, regularly scanning for vulnerabilities, and keeping server security up to date are essential steps in defending against SSL vulnerabilities.
SSL certificate management is an important aspect of website security. To ensure the secure authentication process, it is crucial to follow best practices in managing SSL certificates.
First and foremost, organizations should obtain SSL certificates from trusted authorities. These authorities are responsible for verifying the identity of the website owner, making sure that the certificate is authentic and secure. By obtaining a certificate from a trusted authority, organizations can establish trust with their users and protect against potential cybercriminal activities.
Regularly updating SSL certificates is another best practice. Cybercriminals are constantly evolving their techniques, and vulnerabilities can be discovered over time. By keeping SSL certificates up to date, organizations can address any potential SSL vulnerabilities before they are exploited by hackers.
Implementing strong encryption is also crucial for SSL certificate management. Encryption ensures that data transmitted between the user and the website is securely protected. By using strong encryption algorithms, organizations can prevent unauthorized access to sensitive information.
In addition to obtaining SSL certificates and maintaining strong encryption, organizations should also regularly monitor for potential SSL vulnerabilities. This can be done by employing specialists or coordinators who can analyze and identify any weaknesses in the SSL system. By proactively identifying and addressing vulnerabilities, organizations can enhance their website security and protect against potential threats.
The SSL secure authentication process is paramount to establishing a secure connection between a user and a website. It involves several steps to ensure the authenticity and trustworthiness of the website.
The process begins with a handshake between the user’s browser and the website’s server. During this handshake, the server presents its SSL certificate, which contains the public key necessary for encryption. The user’s browser then verifies the authenticity of the certificate by checking if it is signed by a trusted authority.
Once the certificate is verified, the user’s browser and the server engage in an encrypted communication, protecting data exchanged between them from potential hackers. This encrypted communication is established through the use of symmetric key encryption, where a unique session key is generated for each user session.
During the SSL secure authentication process, the user’s browser also verifies the website’s identity. This is done by checking if the website’s domain matches the information present in the SSL certificate. The user’s browser also checks if the SSL certificate is still valid and has not expired.
By authenticating the website and establishing a secure connection through encryption, the SSL secure authentication process ensures that users can safely trust the website they are interacting with. This process plays a critical role in protecting against cybercrime and ensuring internet security.
An SSL certificate is a digital certificate that authenticates the identity of a website and enables a secure, encrypted connection between the website and the user’s browser.
SSL certificate management is important because it helps ensure the security and privacy of data transmitted between a website and its users. It helps prevent unauthorized access, data breaches, and information theft.
Some best practices for SSL certificate management include regularly monitoring and auditing certificates, keeping track of expiration dates, renewing certificates in a timely manner, using strong encryption algorithms, and properly configuring certificate revocation lists.
SSL certificates should typically be renewed before they expire, as most certificates have a validity period of 1-2 years. It is recommended to renew certificates at least 30 days before the expiration date to avoid any potential disruption in service.
Certificate revocation is the process of invalidating a previously issued SSL certificate before its expiration date. It is important because it allows the website owner to quickly revoke a certificate in the event of a security breach or if the private key associated with the certificate is compromised.
Yes, there are several tools and services available to assist with SSL certificate management. These include certificate management platforms, certificate authorities, and automated certificate renewal services. These tools can help simplify the process of managing and renewing SSL certificates.