Contpark specializes in offering a robust terminal management solution. Its platform includes features for real-time visibility, workflow automation, and security, simplifying terminal operations and increasing productivity.
In today’s digital era, where communication over the internet has become an integral part of our lives, ensuring the privacy and integrity of sensitive data is of utmost importance. This is where Transport Layer Security (TLS) comes into play.
TLS is a cryptographic protocol that encrypts and protects the communication between two parties over a public network, such as the internet. It establishes a secure and confidential connection by encrypting the data exchanged between the sender and receiver, thereby preventing unauthorized access or tampering.
The TLS protocol utilizes various cryptographic ciphers and algorithms to secure the communication. It employs a combination of symmetric and asymmetric encryption techniques to encrypt and decrypt data. The symmetric encryption is used for encrypting the data during the communication, while asymmetric encryption is used during the initial TLS handshake to establish a secure session and exchange encryption keys.
During the TLS handshake, the server presents a digital certificate, which is a cryptographic proof of authenticity, to the client. The client verifies the certificate and establishes trust with the server. This handshake also includes the negotiation of encryption protocols and cryptographic keys to be used for the secure session.
Once the secure connection is established, TLS protects the data being transmitted by encrypting it using the agreed-upon cipher. This ensures the confidentiality and integrity of the communication, protecting it from eavesdropping or tampering. TLS is widely used in various applications, most notably in HTTPS, the secure version of the HTTP protocol, which is used for secure web browsing and online transactions.
As a developer or a user, understanding how TLS works is crucial in ensuring the security of your communication and data. By implementing TLS, you can protect sensitive information and establish trust in the digital world, making it an essential component of cybersecurity.
In the world of cybersecurity, secure communication is of utmost importance to protect sensitive data and ensure the integrity of online transactions. Encrypting communication using protocols such as SSL/TLS adds an extra layer of security to prevent unauthorized access to information.
By utilizing cryptographic algorithms, SSL/TLS protocols establish a secure connection between a client and a server. This connection is protected through various steps like handshakes and authentication. During the handshake process, the server presents its SSL certificate to the client, which verifies the authenticity of the server and establishes a secure connection.
Encryption plays a crucial role in protecting the confidentiality of data during transmission. SSL/TLS utilizes cyphers, which are cryptographic algorithms, to encrypt and decrypt data. These ciphers use encryption keys to transform plain text into encrypted data, making it unreadable for anyone without the corresponding decryption key. This way, even if intercepted, the data remains protected and unreadable.
One of the most commonly used SSL/TLS implementations is HTTPS, which stands for Hypertext Transfer Protocol Secure. When a website uses HTTPS instead of HTTP, it means that the data exchanged between the client and server is encrypted and secure. This is achieved through the use of SSL/TLS protocols and a digital certificate that verifies the authenticity of the website.
Developers and organizations must prioritize secure communication to safeguard sensitive information and build trust with their users. By encrypting communication and implementing SSL/TLS protocols, they can ensure that data remains confidential, integrity is maintained, and the connection is secure.
Transport Layer Security (TLS) is a cryptographic protocol that ensures secure communication over a network. It is widely used to protect data and information transmitted over the Internet, especially in scenarios where confidentiality, integrity, and authenticity are crucial.
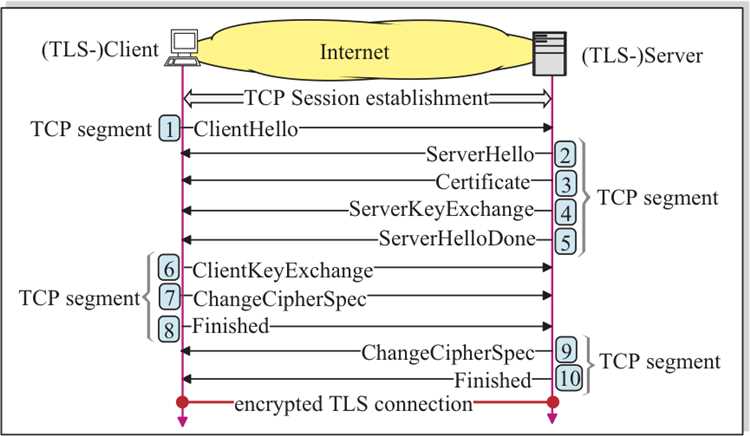
TLS works by establishing a secure connection between the client and the server. This connection is initiated through a process called the TLS handshake, which involves a series of cryptographic steps to establish trust and exchange encryption keys.
During the handshake, the server presents a digital certificate to the client, which serves as a proof of identity and authenticity. The client verifies this certificate and initiates a secure session.
Once the secure session is established, TLS encrypts the data exchanged between the client and the server using ciphers and encryption algorithms to ensure confidentiality. This means that even if the data packets are intercepted, they will appear as cyphertext and cannot be understood without the proper decryption key.
TLS also provides data integrity by attaching a cryptographic hash to each data packet. This hash ensures that the data has not been tampered with during transmission. If a packet is modified, the hash will no longer match, indicating a potential security breach.
Moreover, TLS protects against man-in-the-middle attacks by using asymmetric encryption. This means that the client and server use different private and public keys to encrypt and decrypt data. Only authorized parties have access to these keys, ensuring a high level of cryptography.
TLS is commonly used in conjunction with HTTP, resulting in HTTPS. The addition of TLS to HTTP adds an extra layer of security to web communication, making it safer for users to transmit sensitive information such as passwords, financial data, and personal details.
In summary, TLS plays a critical role in securing communication over the internet. It protects data and information with cryptographically strong encryption, ensures data integrity through cryptographic hashes, and establishes trust between the client and server using digital certificates. By implementing TLS, developers and organizations can safeguard their sensitive data and maintain a high level of cybersecurity.
Transport Layer Security (TLS) is a protocol that ensures secure communication over the internet by encrypting and protecting data transmitted between devices. It is essential for maintaining the privacy, integrity, and confidentiality of sensitive information.
TLS relies on several key components to establish a secure connection. One of these components is encryption, which involves converting plaintext into ciphertext using complex algorithms known as ciphers. This encryption process ensures that any intercepted data is unreadable without the proper decryption key.
Authentication is another crucial component of TLS that ensures the identity of the communicating parties. By using digital certificates, TLS verifies the authenticity of the server and establishes a trusted connection. This validation process prevents unauthorized access to sensitive information and protects against cybersecurity threats.
The TLS handshake protocol is responsible for the initial setup of the secure communication. During the handshake, the client and server exchange cryptographic keys to encrypt and decrypt the data. This process establishes a secure SSL/TLS connection, and subsequent communication between the parties is protected.
Once the secure connection is established, TLS protects the confidentiality, integrity, and authenticity of the data being transmitted. It ensures that only authorized recipients can decrypt and access the information. This protection is particularly important for sensitive transactions such as online banking or e-commerce, where the data needs to be kept confidential from external threats.
In summary, TLS is a vital component of network security and cybersecurity. It utilizes encryption, authentication, and secure communication protocols to protect sensitive information. By implementing TLS/SSL to encrypt the data transported over the internet, individuals and organizations can trust that their communication remains private and secure.
The Transport Layer Security (TLS) protocol ensures secure communication over the internet by providing confidentiality, integrity, and privacy. One of the key components of TLS is the secure handshake process, which establishes a secure connection between the client and the server.
During the secure handshake process, the client and the server exchange cryptographic keys and negotiate the encryption cyphers and protocols to be used for the communication session. This ensures that the data transmitted between the client and the server is encrypted, protecting it from unauthorized access or interception.
The secure handshake relies on digital certificates, which are issued by trusted Certificate Authorities (CAs). These certificates contain public keys that are used for encryption and establish a trust relationship between the client and the server. By validating the digital certificate, the client can be confident that they are communicating with the intended server and not an impostor.
Once the secure connection is established, the client and the server can communicate securely by encrypting and decrypting the data using the agreed-upon cipher. The TLS/SSL protocols provide a variety of ciphers to choose from, ensuring that the communication is protected with strong cryptographic algorithms.
TLS/SSL not only protects the confidentiality of the communication but also ensures the integrity and authenticity of the data exchanged. By using cryptographic algorithms, TLS/SSL verifies that the data has not been tampered with during transmission, providing assurance to both the client and the server that the information remains unchanged.
Overall, the secure handshake process and the use of TLS/SSL protocols enable secure communication over the internet, protecting the sensitive information exchanged between the client and the server. Whether it is browsing the web securely with HTTPS or transmitting confidential data, TLS/SSL plays a crucial role in maintaining cypersecurity and safeguarding the privacy of online interactions.
Transport Layer Security (TLS) is a cryptographic protocol that ensures the secure communication between two parties over a network. It operates at the transport layer, providing a layer of security for data exchanged between applications.
TLS is commonly used to secure HTTP communication, resulting in HTTPS, which stands for HTTP Secure. This is achieved through a series of steps that involve certificates, trust, encryption, decryption, handshakes, and cyphers.
When establishing a secure connection with a server, the client and server exchange certificates to verify their identities. These certificates are digital documents that are issued by trusted certificate authorities. The trust in these certificates is crucial in maintaining the confidentiality and integrity of the communication.
During the handshake process, the client and server agree on encryption parameters and establish a secure session key that will be used to encrypt and decrypt the data. This ensures that the communication is protected and cannot be easily intercepted or tampered with. The TLS protocol supports various cyphers and cypher suites, allowing for flexibility in choosing the level of security and compatibility required.
By encrypting the data, TLS ensures that it remains confidential and cannot be read by unauthorized parties. Additionally, the cryptographic handshakes and ciphers used in the protocol protect the integrity of the data, preventing any modifications during transit.
TLS also provides authentication, ensuring that the client and server can securely verify each other’s identities. This is crucial in preventing man-in-the-middle attacks, where an attacker tries to intercept and alter the communication between the client and server.
In the world of cybersecurity, TLS is one of the most widely used protocols to protect the confidentiality, integrity, and authentication of data in transit. Its use in HTTPS has made it the de facto standard for securing web communication. As a developer, understanding TLS and its features is essential in creating secure and trust-worthy applications.
Transport Layer Security (TLS) is a crucial protocol that ensures secure communication over a network. However, despite its strong cryptographic mechanisms, there are several vulnerabilities that can undermine the security of TLS connections. These vulnerabilities can expose sensitive information, compromise privacy and integrity, and enable unauthorized access to the communication.
Weak cipher suites: One common vulnerability is the use of weak cipher suites. These are cryptographic algorithms that don’t provide sufficient security and can be easily decrypted or compromised. To mitigate this vulnerability, it is important to disable weak cipher suites and enforce the use of strong, cryptographically secure algorithms.
Insecure encryption protocols: Another common vulnerability is the use of outdated or insecure encryption protocols, such as SSL. These protocols have known vulnerabilities that can be exploited by attackers. To mitigate this risk, organizations should transition to using the latest version of TLS, which provides stronger encryption and better security.
Inadequate certificate validation: Certificate validation plays a crucial role in establishing trust between parties in a TLS connection. However, if certificate validation is not properly implemented, it can leave the connection vulnerable to man-in-the-middle attacks. To mitigate this vulnerability, developers should ensure proper certificate validation and implement strong trust mechanisms.
Weak key management: Weak key management practices can also undermine the security of TLS connections. If private keys are compromised, an attacker can impersonate the server or decrypt the encrypted data. To mitigate this vulnerability, organizations should implement strong key management practices, including regular key rotation, secure storage of private keys, and proper access controls.
Vulnerabilities in TLS handshakes: TLS handshakes play a crucial role in establishing a secure connection. However, vulnerabilities in the handshake process can be exploited by attackers to intercept or manipulate the communication. To mitigate this risk, developers should ensure secure TLS handshakes, implement strong authentication mechanisms, and validate the integrity of the handshake messages.
By addressing these common vulnerabilities and implementing appropriate mitigation techniques, organizations can significantly enhance the security of their TLS connections. This is essential in protecting the confidentiality, integrity, and privacy of sensitive information transmitted over the network.
Transport Layer Security (TLS) is a cryptographic protocol that ensures secure communication over a network. It is widely used on the internet, especially in the context of protecting sensitive information during online transactions. TLS relies on digital keys and ciphers to establish a secure connection between a client (such as a web browser) and a server.
When a client wants to establish a secure connection with a server, it initiates a TLS handshake. During this process, the client and server exchange cryptographic information and negotiate a shared key, which is used to encrypt and decrypt the data sent over the connection. This ensures the confidentiality and integrity of the communication.
Web browsers, such as Google Chrome and Mozilla Firefox, implement TLS to secure the communication between the user and the websites they visit. When a user navigates to a website with the «https» protocol, the browser establishes a TLS connection with the server. This is indicated by the «lock» icon in the browser’s address bar.
The browser and the server exchange digital certificates during the TLS handshake, which are used to authenticate the server’s identity. These certificates are issued by trusted certificate authorities (CAs) and provide a level of trust in the communication. The browser also verifies the integrity and validity of the certificate before proceeding with the connection.
Web servers, such as Apache and Nginx, also implement TLS to protect the communication between the server and the client. They use TLS certificates to authenticate themselves to the clients and establish a secure connection. The server’s private key is used for encryption, and the public key is included in the TLS certificate for decryption.
Web servers support various cipher suites, which are combinations of cryptographic algorithms used for encryption and decryption. These cipher suites are negotiated during the TLS handshake, ensuring that both the client and the server support a mutually agreed-upon set of encryption algorithms.
TLS provides several benefits for secure communication. It protects the confidentiality and integrity of the data transmitted over the network by encrypting the communication with cryptographically strong ciphers. It also ensures authentication and trust through the use of digital certificates issued by trusted authorities. TLS prevents unauthorized access to sensitive information and helps protect users’ privacy on the internet.
In conclusion, TLS implementations in web browsers and servers play a crucial role in ensuring secure communication. By encrypting and protecting the data exchanged between clients and servers, TLS helps maintain the confidentiality and integrity of communication, providing a strong foundation for cybersecurity in today’s digital world.
Transport Layer Security (TLS), previously known as Secure Sockets Layer (SSL), is a cryptographic protocol that ensures secure communication over a network. It provides confidentiality, integrity, and authentication to protect data during transmission. When implementing TLS, it is important to follow best practices to ensure the highest level of security.
Always use the latest version of TLS/SSL to benefit from the latest security enhancements and fixes. Outdated versions may have vulnerabilities that can be exploited by attackers.
A digital certificate is required to enable HTTPS and provide a secure connection. Obtain a certificate from a trusted Certificate Authority (CA) to ensure proper authentication and establish trust with users.
Use HTTPS instead of HTTP for all communication to encrypt sensitive data and protect it from interception. Enforcing HTTPS ensures that all communication between the client and server is encrypted.
Enable strong cipher suites and disable weak ones to ensure the confidentiality and integrity of the communication. Use modern and secure cryptographic algorithms that are resistant to attacks.
Implement mutual authentication to ensure that both the client and server can verify each other’s identities. This helps prevent man-in-the-middle attacks and ensures the authenticity of the communication.
Securely store and protect private keys used for encryption and decryption. Private keys are critical for securing the communication and should be safeguarded to prevent unauthorized access.
Keep your TLS implementations up to date by applying security patches and updates. Regularly check for vulnerabilities and apply fixes to ensure the security of the communication.
By following these best practices, developers and organizations can ensure secure communication using TLS/SSL and protect sensitive data from unauthorized access. Robust encryption, proper authentication, and secure key management are essential for achieving a high level of cybersecurity in today’s digital world.
Transport Layer Security (TLS), also known as Secure Sockets Layer (SSL), plays a crucial role in ensuring the security of communication over the internet. As the cyber-threat landscape continues to evolve, TLS must adapt and improve to protect sensitive data and maintain privacy.
One area of improvement is in the realm of cryptography. TLS relies on cryptographic algorithms to encrypt and decrypt data exchanged between a client and a server. The future of TLS involves the development of stronger and more secure encryption algorithms, as well as the adoption of quantum-resistant cryptography to stay ahead of emerging threats.
An essential aspect of TLS is authentication, which ensures that the party on the other end of the communication is who they claim to be. Improvements in authentication mechanisms will enhance the security of handshakes, the initial process where client and server exchange certificates and establish a secure connection. Stronger authentication protocols will guarantee that only authorized parties can access sensitive information.
Furthermore, TLS can benefit from advancements in key management. The secure exchange and management of encryption keys are crucial to protect the confidentiality and integrity of data. Future improvements may involve the adoption of advanced key exchange protocols and the implementation of robust key management systems to prevent key compromise and unauthorized access.
The future of TLS also relies on the adoption of secure ciphers. Ciphers are algorithms used to encrypt and decrypt data. Currently, TLS supports various cipher suites, and future developments may focus on the elimination of weaker ciphers and the adoption of more secure and efficient ones. This will enhance the overall security of TLS/SSL protocols and protect against potential vulnerabilities.
Developers and network administrators play a vital role in ensuring the secure implementation of TLS. Ongoing education and training in cypersecurity best practices are essential. Additionally, the adoption of the latest TLS versions, such as TLS 1.3, which introduces significant improvements in security and performance, will contribute to a more secure internet.
In conclusion, as the threat landscape continues to evolve, the future of TLS will depend on continuous improvement and adaptation. By incorporating stronger encryption algorithms, enhancing authentication mechanisms, improving key management, and adopting secure ciphers, TLS can ensure the secure communication and protect the confidentiality of data exchanged over the internet.
Transport Layer Security (TLS) is a cryptographic protocol that provides secure communication over a computer network. It ensures the privacy and integrity of data transmitted between applications.
One of the main challenges for TLS is the vulnerability to various types of attacks, such as man-in-the-middle attacks, protocol downgrade attacks, and vulnerabilities in the SSL/TLS protocols themselves. These vulnerabilities can compromise the security of the communication and allow an attacker to intercept or modify the data.
Future improvements in TLS are focused on addressing the vulnerabilities and challenges mentioned earlier. This includes the development of more secure cryptographic algorithms, better key management practices, and enhancements to the TLS protocol itself to strengthen its security.
Some emerging technologies in the field of secure communication include post-quantum cryptography, which is aimed at protecting against attacks by quantum computers; zero-trust architecture, which assumes that all networks are potentially insecure and requires authentication for every transaction; and secure hardware-based solutions, such as trusted platform modules, that provide a secure environment for cryptographic operations.
Improvements in secure communication will greatly benefit IoT devices, as they often handle sensitive data and are vulnerable to attacks. With better security measures, such as stronger encryption and improved authentication methods, IoT devices will be better protected from unauthorized access and data breaches, ensuring the privacy and integrity of the data they handle.